
 FALL 2000
FALL 2000
Lecture Notes 11:
NETWORK MANAGEMENT
A few beginning concepts – you probably know this stuff – but it won’t hurt to review.
Networking is a means of connecting computers together so they can share- Data, such as files and programs
- Resources, such as printers and modems
Each computer or workstation on a network is called a network station, a node, or possibly a host. Each processor classifies other processors and their resources as remote, and considers its own resources as local.
Typically, a host at one site, called the server, has resources that a host at another site, called the client, wants to use. Hosts can alternate being clients and servers. Data is sent over the network as bits and bytes
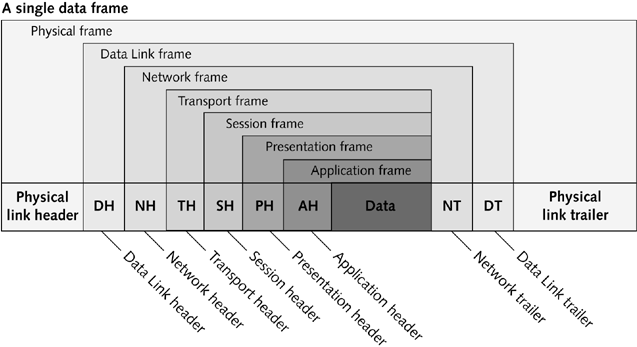
Data to be sent over the network is first divided into segments, each with a header and trailer
- A header is information sent in front of data to identify the data destination and protocols
- A trailer follows the data and contains information used by some protocols for error checking
- The entire unit is called a packet or a frame
Data packets or frames are sent as independent units over the network. At the receiving end, the header and trailer information is removed, and the data is reassembled.For PCs, the network card breaks the data into segments and adds the header and trailer, creating the packets.
LAN (local area network)
- Typically located in a single building or adjacent buildings
- Having nodes connected by cables
WAN (wide area network)
- Cover a large geographical area, such as a multi-campus university
- Nodes may be connected by methods other than just cables, such as microwave signals
The 3 most popular physical network architectures, or topologies,are
- Ethernet
- Token Ring
- FDDI (Fiber Distributed Data Interface)
Architectures are distinguished basically by
- How computers are logically connected
- How traffic is controlled on the network
Ethernet is the most popular network topology used today.
- Bus network- connects each node in a line with no centralized point of connection.
- Star network- uses a hub, a device that provides a central location through which the cables of all the computers on the network are connected.
The star is the more popular Ethernet configuration.
The Token Ring is logically a ring, but stations are physically connected to the network in a star formation.
- Each station connects to a centralized hub called a controlled-access unit (CAU), multistation access unit (MAU), or smart multistation access unit (SMAU).
- Communication and traffic are controlled by a token, a small frame with a special format, that travels in one direction.
FDDI (Fiber Distributed Data Interface)
A ring-based network without a centralized hub, making it a physical and logical ring. Uses a token-passing method to control traffic, but is more powerful and sophisticated than Token Ring. Stations can pass more than one frame along the ring without waiting for the first to return. Possessing the token gives a station the right to transmit. Data frames travel along the ring without the token. A station holds the token until it has sent its data, then passes the token on. More than one station can have frames on the ring at the same time.
Network Interface Card (NIC)
- Plugs into a systemboard.
- Provides a port or ports on the back of the card for connection to the network.
- May be designed as an Ethernet card, Token Ring card, or FDDI card.
- Manages communication and network protocol for the PC.
TRANSPORT PROTOCOL STANDARDS
OSI Layer Network Model
International Organisation of Standardization (makes recommendations about data communications) took on the task of creating such a network architecture (OSI reference model). Is a framework for defining services network should provide to users. The word "open" means that any two systems that conform to the reference model and the related standards can be connected, regardless of the platform.
Once all services were identified, similar clusters were collected together in layers. Reason for doing this was to group easily localised functions so that each layer could be re-designed and its protocols changed in any way to take advantage of new advances without changing the services to and expected from other layers.
Boundaries between layers were selected at points that past experience suggested were effective.
Data is segmented into frames or packets for transmission. Each layer in the seven layer model can add information to the beginning and ending of a frame, as below: When the frame is presented to the receiving station, that layer interprets the information in the header and trailer intended for that layer, and then strips off the information before passing the frame onto the next higher layer in the model. For frames to transmit successfully, each layer of the OSI model must communicate with the same protocol as its counterpart in the remote computer.
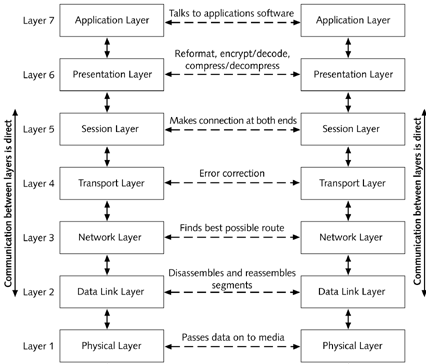
LAYER 1 The Physical Layer
This is the protocol for how the data is transmitted.Sees the data as only bits that need to be passed on. This is the only layer concerned with hardware. The packaging of data has already occurred before this layer ; the physical layer does not distinguish the header from the rest of the package – just see all of it as bits that need to be passed on.
LAYER 2 The Data Link Layer
Responsible for receiving frames of data from the Network layer and splitting them into segments of bits to be presented to the Physical layer for transport. Software is needed to implement this layer. The data link layer establishes and controls the physical path of communication before sending data to the physical layer. Error checks in both directions. Looks for errors in transmission, and damages, lost or duplicate message frames. Token Ring or Ethernet firmware on network cards are examples of code that handles Data Link and Physical Layers.LAYER 3 The Network Layer
Software at this level accepts blocks of data from Layer 4, the transport layer, resizes them to shorter packets and routes them to the proper destination.Responsible for finding the best route by which to send frames over a network
Addressing methods that allow a node and its network to be identified, as well as algorithms to handle address resolution are handled.
The most common protocols are TCP/IP (Transmission Control Protocol/Internet Protocol) and IPX/SPX (Internetwork Packet exchange/ sequenced packet exchange). For TCP/IP, the TCP portion is responsible for error checking, and therefore operates in the Transport layer and the IP portion makes up the network layer and is responsible for routing. , (we will talk more about these later). WinNT and Win98 support both protocols, Novell supports IPX/SPX.
LAYER 4 The Transport Layer
Maintains reliable data transmission between end users. This layer also has a mechanism to ensure that a fast host cannot overrun a slow terminal.LAYER 5 The Session Layer
Responsible for establishing and maintaining a session between two networked stations or nodes.A session between two nodes in a network is sometimes called a socket.
Transport layer and session layer are very similar, and OS of host computer handles session layer they are often combined into one as in TCP/IP.
Layer 6 The Presentation Layer
Receives requests for files from the Application layer and presents the requests to the Session layer.Responsible for data manipulation functions – formatting, compression and encryption. Also data conversion, syntax conversion and protocol conversion.
Accommodates totally different interfaces as seen by a terminal in one node and expected by the application program at the host computer.
Layer 7 The Application Layer
Responsible for interfacing with the applications software that is using the network.Responsible for formatting user data before passing it on to the lower layers for transmission. It contains network management functions such as file transfer and e-mail.
NETWORKING SOFTWARE
Each layer in the OSI model uses a different method of communicating to its counterpart layer
- The Physical and Data Link layers are controlled by firmware
- Most of the other layers are controlled by the OS managing the network
The 3 best-known PC network operating systems are UNIX, NetWare by Novell, and Microsoft Windows NT
Network protocol:
Point-to-Point Protocol (PPP) is a protocol by which PCs with modems can connect to a networkIt is the most popular protocol for managing network transmission from one modem to another
At the Network and Transport layers, TCP/IP is a protocol used by the Internet
E-mail is sent using SMTP (Simple Mail Transfer Protocol), which operates on the Session layer. Network drives use NFS (Network File Service) protocol, and the World Wide Web uses HTTP (Hypertext Transfer Protocol), both on the Session layer. Transferring files across the Internet is usually done using FTP (File-Transfer Protocol)
Network services provided at the application and presentation levels are:
- Web Browser: - Provides primary access to the Internet
- Chat rooms: - Provide on-line, interactive communication among several people on the Internet
- E-mail: - Provides electronic mail (which largely consists of text files) across the Internet or other networks
- FTP: - Provides a method of transferring files from one computer to another
- Telnet: - Provides a console session from a computer to a remote computer
- Print services: - Refers to sharing printers across a network
- Network drive: - Hard drive space on one computer on the network made available to another as a virtual or logical drive
MANAGEMENT OF NETWORK FUNCTIONS
Early networks focussed on sharing expensive hardware such as large mainframes, laser printers and sizable hard disks. System owners soon realized that the real value of a network was not the hardware but the information. Operating systems were enhanced with network capabilities. Network operating systems include networking as an integral part of the operating system, not as an extension of it. A network operating system has to address the issues of memory, device, processor and file management for the network.
MEMORY MANAGEMENT
M.M. tracks available memory on each node by use of kernel that performs paging based on the goals of the local system.
Policies and mechanisms implemented at the local sites will be driven by global system requirements.
At the network level, memory manager receives requests from the process manager to provide memory to new or expanding client or server processes.
MM’s function extended from that of controlling the local machine to accept requests for memory from both local and global sources.
Combined memory of entire system made up of several subpools, one for each processor – network MM has subcomponent that exists on each machine.
PROCESS MANAGEMENT
The creation of a process by a network operating system involves the creation of a PCB with similar info but with additional info to indicate the location of the process in the network. The deletion or termination of a process requires finding the PCB and having the authority to access and delete it.
High level of cooperation maintained in system sites in determining which process should be loaded and where it should be run. Once the process has been scheduled for service, must be initiated at assigned site, requiring a dispatcher, which allocates the device to the process and initiates its execution. This may even involve:
- Moving a process in memory from one site to another.
- Reorganizing a site’s memory allocation
- Reorganizing a site’s ready, running and waiting queues
Interrupts may require service from IO outside the site and the process manager in a network system would have to handle this.
DEVICE MANAGEMENT
Performed at the physical level same as for workstation OS. Network OS must keep a global accounting of devices and their availability, maintaining each devices status and control blocks and distributing this info to all sites. Systems are configured around server processes, which manage multiple resources. A server process consists of device driver, device manger and network server component.
FILE MANAGEMENT
Goal of networked file management is to give illusion of a single logical file system implemented an assortment of devices and computers.
Network OS must manage the files in the same way as single user OS. Should read, write, open, close, create and delete files. However, all potential users of files must be locked out of files being currently used by other users.
NETWORK MANAGEMENT
Interprocess communication is transparent to the users of the network. The Network manager has the function of controlling the allocation of ports to processes, identifying the processes in the network, controlling the flow of messages. Relieves users of having to know where processes physically reside in the network. Network manager accepts each process’s send and receive commands and interprets them, transforms these commands into low level actions that perform the transmission of messages over the links.
WinNT Networking
Windows NT Server
Has all the functionality of Windows NT Workstation - Offers the additional functionality of administering and monitoring the network from a centralized locationBoth Windows NT Workstation and Server can be configured to work as one node in a workgroup or as one node on a domain.
Workgroup
- A logical group of computers and users that share resources
- Can be made up of computers that use either Workstation or Server
- The control of administration, resources, and security is distributed throughout the network
- Every computer has its own directory database of user accounts and security policies
- Each computer manages the accounts on that computer for other users and computers that want to access the information on it
- A workgroup does not require a Windows NT server to be present
Domain
A Windows NT domain is a group of networked computers thatShare a centralized directory database of user account information and security for the entire set of computersThe backup domain controller (BDC) is a computer that has a backup of the directory database
The primary domain controller (PDC) stores and controls a database of
- User accountsThis database is called the directory database or the security accounts manager (SAM) database.
- Group accounts
- Computer accounts
Used on PCs to control who has access to what programs, files, and other resources on a PC or network
With DOS and Windows 95, there is no all-encompassing security to the PC except the power-on password
Windows NT does provide all-encompassing security to the PC
User accounts, in a workgroup, must be set up on each computer
User accounts, in a domain, can be set up from the centralized domain server
During Windows NT installation, the administrator account is always created
An administrator has the rights and permissions to all computer software and hardware resources
Permissions granted to a user and the user’s OS environment are controlled by the administrator, who can
- Assign restrictions and rights to a group
- Assign individual restrictions and rights
- In Windows NT Server, set profiles for an entire network from his/her PC and allow users to move from PC to PC with their profiles following them (called roaming users)
The Internet
- The largest network in the world
- A web of interconnecting yet independent networks: a network of networks
Most people access the Internet through an Internet Service Provider (ISP) that gives you
- A username and password
- An access phone number
Each node on a network is assigned a unique IP (Internet Protocol) address
- The address is made up of four numbers separated by periodsThe largest IP address is 255.255.255.255
- Each of the numbers is called an octet
- Each number is 8 bits long, so four numbers total 32 bits
- The largest 8-bit number is 11111111, which equals 255 in decimal
IP addresses are divided into three classes
Class A license
- Assigned a single number to be used in the first octet of the address, which becomes the network address
- The first number may be from 0 to 126
- The other 3 octets can be used for host addresses that uniquely identify each host on this network
Class B license
- Assigned numbers for the first two octets
- The first octet is between 128 and 191
- The second octet is between 0 and 255
- The last two numbers can be used for host addresses
Class C license
- Assigned three octets as the network addressStatic IP address
- The first octet is between 192 and 254
- IP address is permanently assigned to a workstation
Dynamic IP address
- The server assigns an IP address to a workstation when it comes on-line to be used for the current session only
- The server that manages dynamic IP addresses uses Dynamic Host Configuration Protocol (DHCP)
A few IP addresses are reserved for TCP/IP
Because of an impending shortage of IP addresses, a new scheme of IP addresses is being developed
- Called IP version 6 (IPv6)
- Uses 128 bits instead of 32; each octet will have 32 bits
- Can automatically assign an IP address to a network device
Domain names are word-based names that can be used to address a host on the Internet, rather than the IP address
A host computer with a certain domain name, connected to one network and assigned a certain IP address, can be moved to another network and assigned a different IP address
The domain name can stay with the host while it connects to either network
Two name resolution services track the relationships between domain names and IP addresses
- Domain Name System (DNS)
- Microsoft’s Windows Internet Naming Service (WINS)
TCP/IP
- Designed to enable routing of data from one network to another over a huge geographical area and over a huge number of networksTCP/IP can use more than one protocol at each OSI layer it supports
- Uses routers to transfer packets of data, datagrams, from network to network making all the networks appear to be one large network
- Is a suite of protocols that includes error checking
When data is being transmitted, only one protocol is used at each layer of the OSI model, depending on the type of data being transmitted and the software interfacing with the network